Configuring the Jamf AD CS Connector (IIS) to Use an Alternate Server Certificate
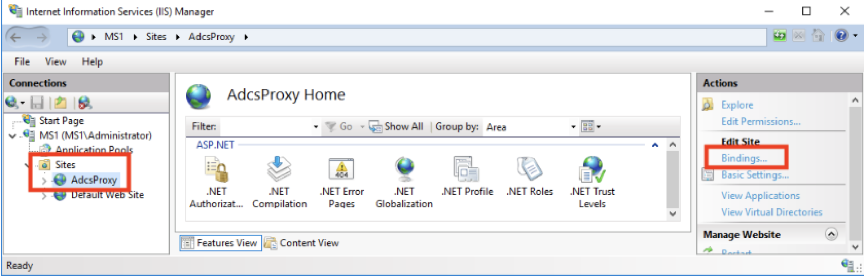
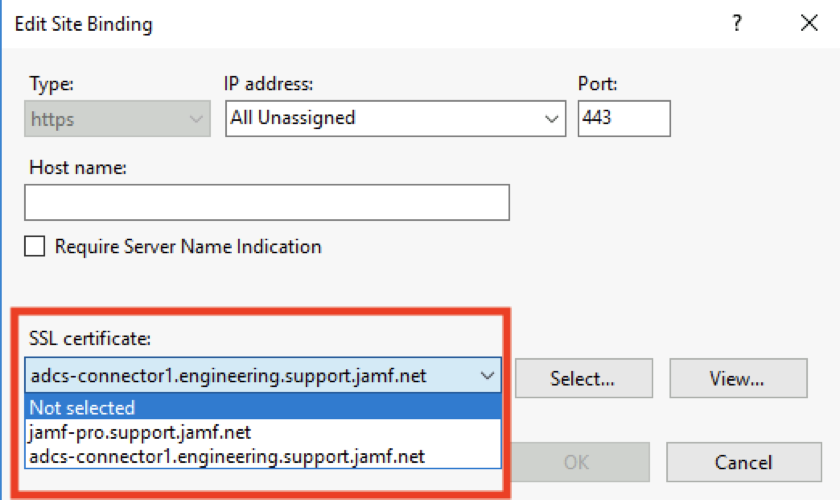
The AD CS connector creates secure server and client certificates when installed. However, if your organization prefers to use certificates created by an internal CA or a 3rd party CA, you can configure the AD CS Connector use alternate server and client certificates.
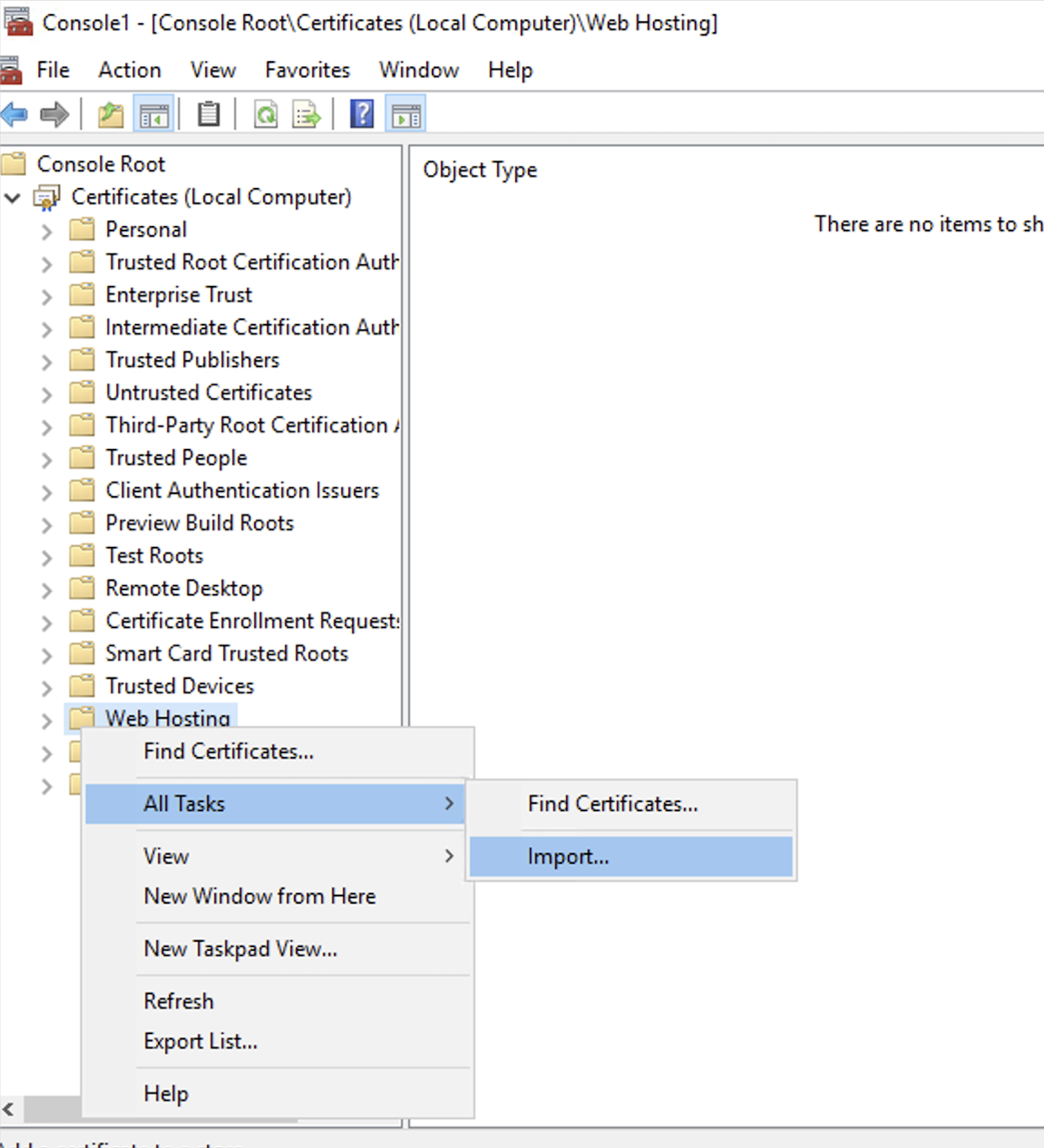
You have the server certificate that you want to use.
The server certificate is in .pfx format (the format is usually provided by your PKI team).
If your identity has root or intermediate certificates in its trust chain that were not included in the .pfx file you added to the Windows certificates store, you must also add them.
Replace your IIS server certificate prior to expiration. If you do not, Jamf Promay no longer be able to negotiate TLS connections after the expiration date has passed. The steps are the same as the initial installation steps.