Configuring Unified Log Filters
The Unified Logging system available in macOS 10.12 or later provides a central location to store log data on the Mac. The Console and Terminal apps allow users to view, stream, and filter this data on computers to manually troubleshoot errors or detect threats.
With Jamf Protect, you can use the same predicate-based filter criteria that are often used with the log command to collect relevant log entries from computers and send them to a security information and event management (SIEM) solution.
Requirement
To use this feature, you need to integrate Jamf Protect with a security information and events management (SIEM) solution.
If your organization uses Splunk, see the Integrating with Splunk section of this guide.
Creating a Unified Log Filter
You must create a predicate-based filter that collects logs relevant to your organization's needs. The following steps show how to use Console to help you identify criteria that can be added to a predicate filter.
-
Open the Console app.
-
Enter key words that are relevant to logs you want view in the search field.
Example: If you want see all logs related to Airdrop file transfers, search "Airdrop".
-
Analyze the results, and continue to refine your search criteria until only logs relevant to your needs are displayed in Console.
Example: To narrow the criteria to just outbound Airdrop transfers, send a file with Airdrop and search for the file name. The returned log entries display additional criteria, such as the process and subsystem that execute the event. The process is "sharingd" and subsystem is "com.apple.sharingd". Both message entries in this example begin with "startSending".
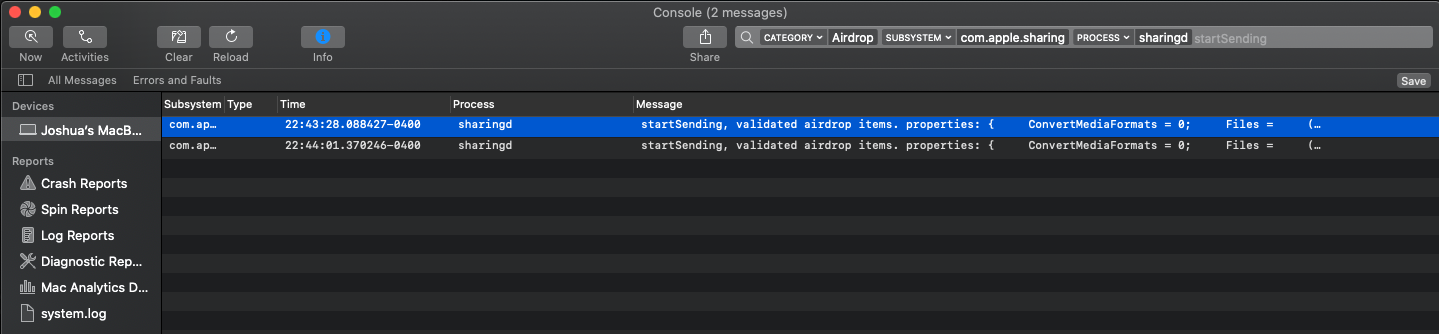
-
Create a predicate-based filter that includes the criteria from step 3. This value will be used to configure a Unified Log Filter in Jamf Protect.
Example: The search criteria that filters for outbound Airdrop transfers in step 3 is written like the following in predicate syntax:
process = 'sharingd' and subsystem = 'com.apple.sharing' and category = 'AirDrop' and composedMessage BEGINSWITH[cd] 'startSending' and logType='info'For a full list of supported keys that can be used in a predicate-based filter, execute the following command: log help predicates
-
(Optional) Confirm that your filter is correct.
-
Use Terminal to execute a log command that uses your predicate.
Example: log stream --predicate process = 'sharingd' and subsystem = 'com.apple.sharing' and category = 'AirDrop' and composedMessage BEGINSWITH[cd] 'startSending' and logType='info'
-
Complete a task on your computer that will generate a log that meets your filter criteria.
-
Confirm that the task generates a new log entry in your Terminal session.
-
You should now have a predicate-based filter that can be used to configure a Unified Log Filter in Jamf Protect.
Adding Unified Log Filters to Jamf Protect
-
In Jamf Protect, click Unified Logging in the sidebar.
-
Click Add New Filter.
-
Give your filter a name.
-
(Optional) Add Tags for your filter.
-
Enter your previously created predicate-based filter.
Note: Only enter the predicate filter between the quotations.The log command and --predicate flag you used to test your filter should not be included.
-
Click Save.
All computers will now send logs that match your filter to your security information and event management (SIEM) solution.
Related Information
For information on content caching logs and statistics, see the following section of Apple's macOS User Guide: https://support.apple.com/guide/mac-help/view-content-caching-logs-statistics-mac-mchl0d8533cd/mac
For related information about Unified Logging and NSPredicate syntax, see the following Apple documentation: